Beginners Guide to Using Windows Sandbox Like a Pro
Last Updated:
Have you ever downloaded a program but didn’t feel safe running it on your PC? Or maybe someone sent you a link but it feels kinda shady?
With how common phishing, malware, and email scams are, these are totally valid concerns.
Windows Sandbox is one of the best ways to stay safe from such threats.
It creates a temporary Windows instance where you can safely open such programs and links.
Since it’s an isolated environment, it’s near-impossible for any threats to escape and affect your actual system.
Let me show you how easy it is to use Windows Sandbox.
What is Windows Sandbox?
Windows Sandbox is much like a real-world kids’ sandbox – an area where you can build, destroy, and experiment without any impact on things outside the sandbox.
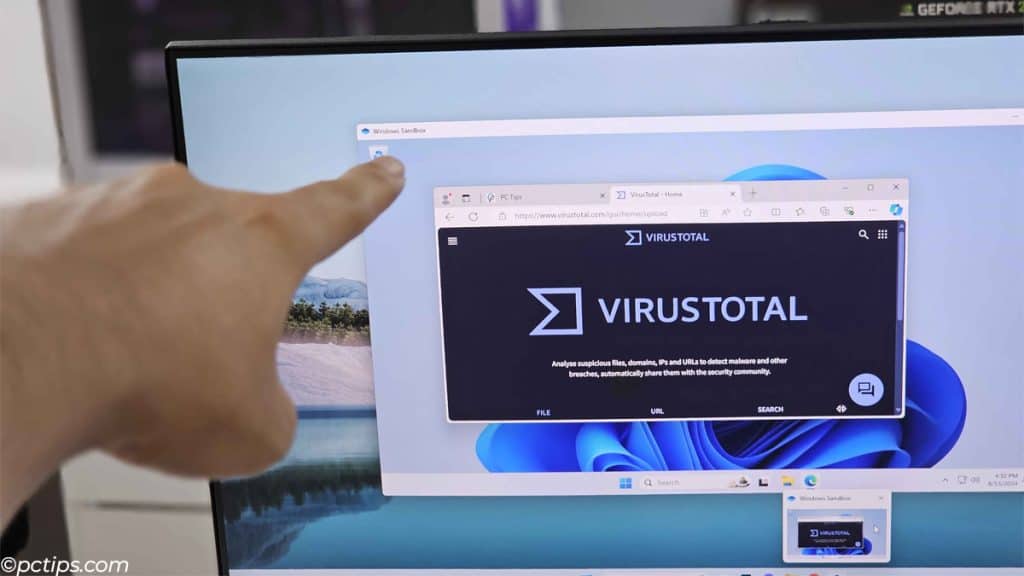
It’s built-in to Windows, extremely light, very quick to launch, and super easy to use.
Anytime you want to perform a task you wouldn’t trust your PC with, fire up a sandbox instance.
It’ll launch in seconds and let you do most things as if you had a second spare computer.
It’s extremely secure as it uses hardware virtualization to isolate the kernel. And It’s disposable too as everything gets discarded when you close it.
This means: Any experimental changes you make or viruses you find remain isolated inside the sandbox. When you close the sandbox, they’ll cease to exist and you’ll get to work with a fresh new instance every time.
Should You Use Windows Sandbox?
This is an impressive feature on paper. But why should it matter to you?
Well, I recently covered the top threats to watch out for in 2024 and these topped the list:
- Malware (ransomware, RATs, worms, spyware) – Ransomware attacks increased by 73% from 2022 to 2023.
- Phishing – 2023 was the worst year in history for phishing attacks with almost 5 million attacks reported.
- Data breach, identity theft, and fraud – Data compromises affected over 353 million people.
You’ll find the complete list of stats and sources in the linked article. But the takeaway was this:
Cyberthreats are increasing every year. Attackers aren’t just targeting businesses and large corporations; they’re going after normal users too!
When you open a link online, download an email attachment, or obtain files from unofficial sources, you are at genuine risk of these threats!
Considering this, sandboxes can be a lifesaver; let me explain how.
How Can Windows Sandbox Keep You Safe?
Here are the main real-world tasks I use Windows Sandbox for:
- to browse web pages that I suspect might be dangerous
- check downloaded email attachments
- test encrypted PDFs and other documents
- test software from third-party websites
- try out programs without installing them on my actual PC
- run keygens
- test downloaded scripts
- provide a temporary private space for other people to use your PC
Programs like browsers or MS Office are a common attack vector on Windows. The same goes for possibly infected files obtained from questionable sources (like torrenting).
If you’re serious about safety, a sandbox is a must-use in such cases.
Windows Sandbox System Requirements
To get started with Windows Sandbox, your computer should meet some basic spec requirements. Here’s the minimum:
- 4 GB RAM
- 2 CPU cores
- 1 GB disk space
- 64-bit architecture
- Windows 10 Pro, Education, or Enterprise build version 18305 or newer
- Virtualization must be enabled in the BIOS
Most modern PCs can fulfill these specs. All that’s left is to enable the necessary features and get started.
How to Enable Windows Sandbox
Windows Sandbox relies on virtualization for isolation (security). So, we’ll start with that:
- Power on your PC. The BIOS key should be marked on the screen (Del works on most PCs). Repeatedly press it until you enter BIOS setup.

- Look for Advanced Settings, Advanced CPU Configuration, or a similar section.
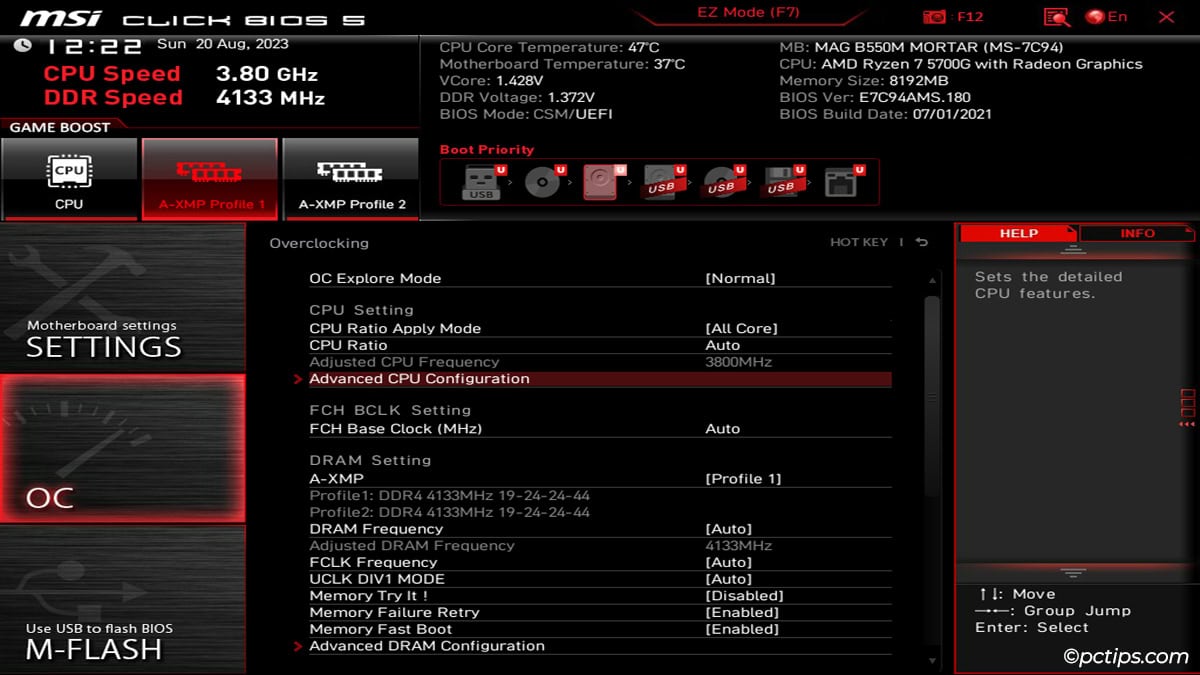
- Look for the virtualization option:
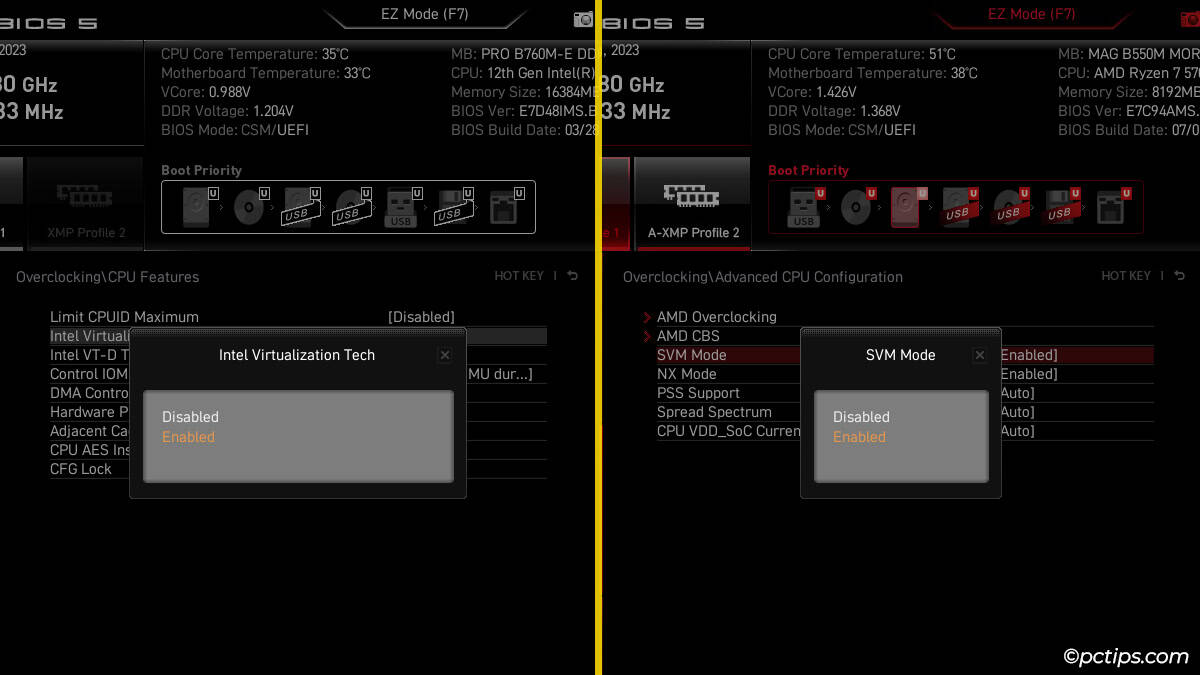
- Intel CPUs – VT-x or Intel Virtualization Technology
- AMD CPUs – SVM
- Enable this option.
- Press F10 to save the changes and exit the BIOS.
The PC should automatically restart. Once Windows loads,
- Press Win + R and enter
optionalfeatures. - Scroll down and enable the Windows Sandbox feature.
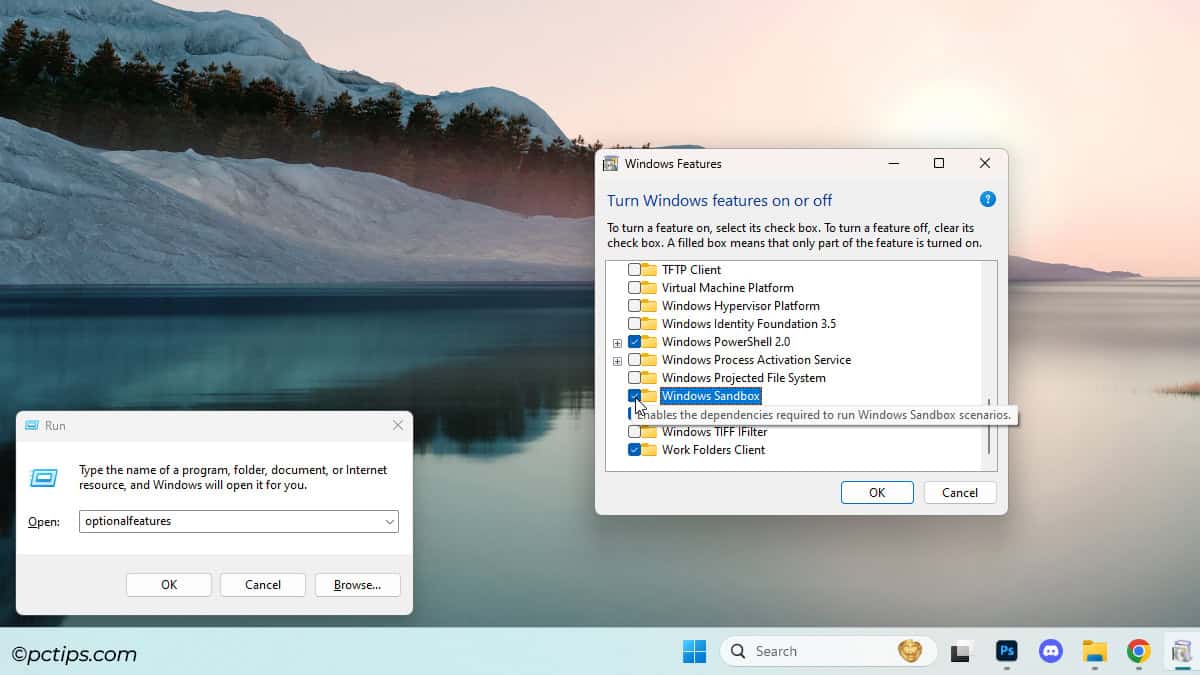
- Reboot the PC when prompted.
CLI Tip: You can also use this one-liner in the Terminal to enable Windows Sandbox:Enable-WindowsOptionalFeature -FeatureName "Containers-DisposableClientVM" -All -Online
Launch Windows Sandbox
Search ‘windows sandbox’ and open the app. You could also pin it to the Taskbar or Start Menu for easier access in the future.
The sandbox should boot within 10 seconds – much faster than a full-featured VM.
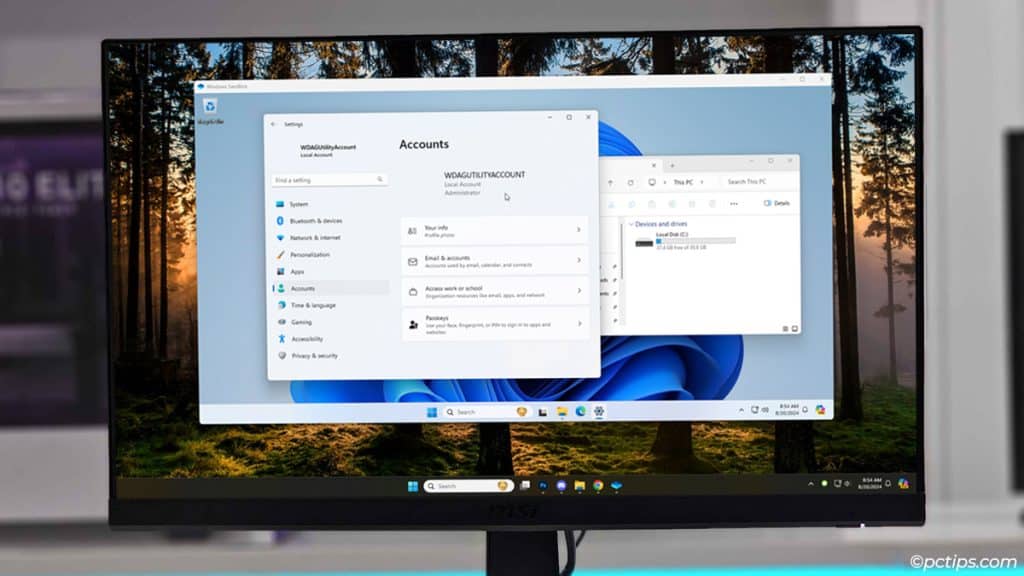
Clipboard redirection and networking are enabled by default. So, you can copy-paste text and files between the sandbox and host (your PC).
You can also access network shares or the internet (all of this is a security risk; we’ll get to that soon).
You’ll also find a Windows Defender Application Guard user account (WDAGUtilityAccount) and a partition of around 40 GBs.
Explore the sandbox for a bit and get familiar with it.
Safe Testing Inside the Sandbox
You might have some single-use files like keygens, documents, email attachments, executables for programs you want to check out, etc.
- Launch Edge inside the sandbox.
- Download the file.
- Open and view/run it inside the sandbox.
- The same goes for sketchy links and websites.
Ideally, the host shouldn’t get exposed to these risky encounters at all; the testing should start and end within the sandbox.
But sometimes, the file will already be on your system. In that case, simply copy it, paste it into the sandbox, and launch it there.
Close the sandbox when you’re done testing.
Diagnose Malware Inside the Sandbox
You can run/view the content of PDFs and keygens inside the sandbox – safe and easy. But for programs, a single run won’t cut it.
You’ll likely test it in the sandbox and install it on the host later. It’s essential to verify that the installer is legit and malware-free.
- Install the program inside the sandbox and monitor it for a while.
- Monitor background processes with Task Manager
- Monitor resource usage and network activity with Resource Monitor
- Check for other infection signs like unfamiliar programs, pop-ups, changed Windows settings, etc
- Some malware will not activate if detects a virtualized environment like a sandbox. So, upload the download link or file to online scanners like VirusTotal or HybridAnalysis too.
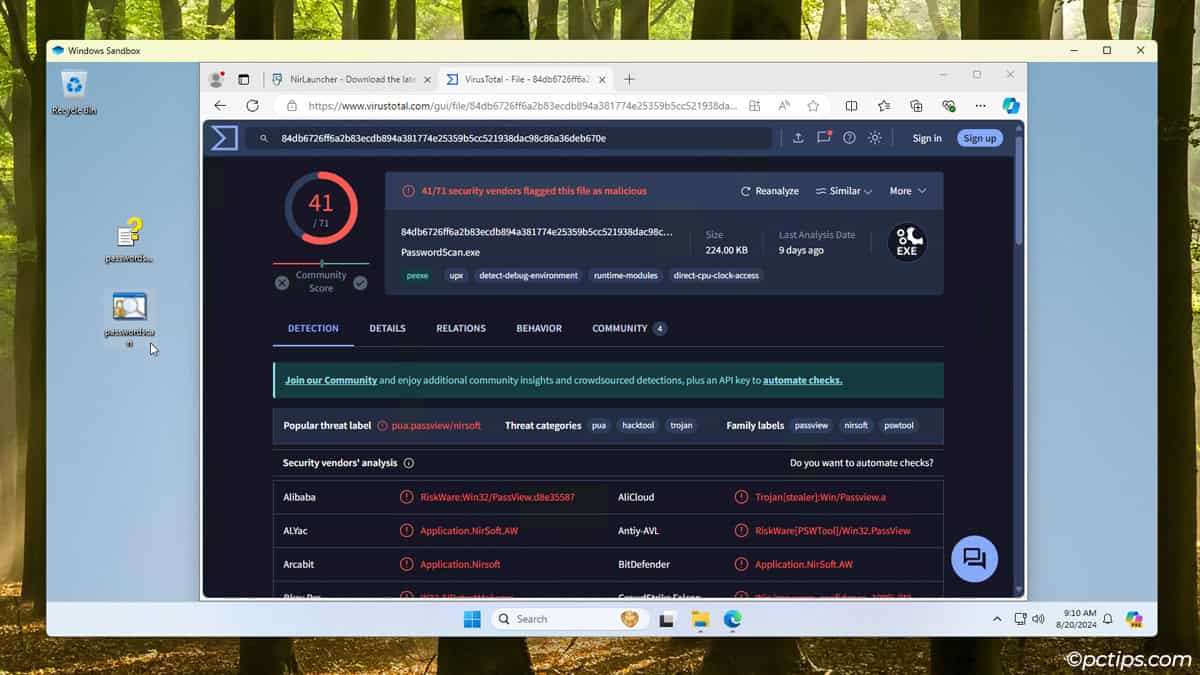
Note: Windows Sandbox was primarily designed for quick testing by normal users and devs. As it was never meant for in-depth or long-term malware diagnosis, it doesn’t excel at that.
Windows Sandbox Configuration
Instead of the default image, you can create a .wsb config file to launch a custom sandbox instance. This lets you-
- Eliminate security risks present in the default image
- Map the host’s folders with specific permissions
- Share the host’s mic, webcam input, printers, and much more
Editing a few simple parameters is all it takes.
Create a Basic Config File
Open Notepad or any other text editor. Enter these tags:
<configuration>
</configuration>Save this file with a .wsb extension (e.g., configfile.wsb).
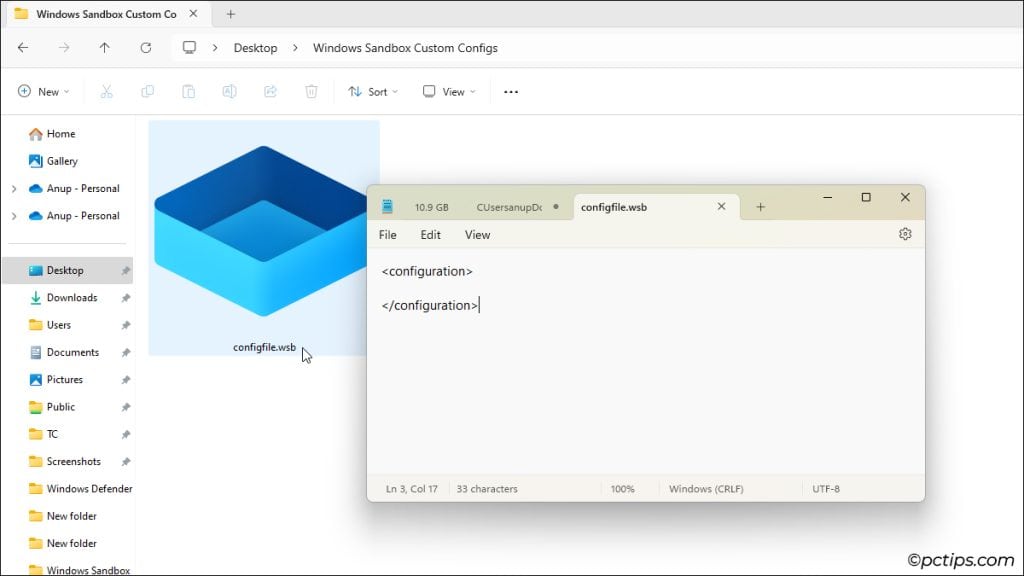
Double-clicking this file will launch a sandbox instance.
You can add parameters between the tags to customize the instance. For instance, you can disable network access like so:
<configuration>
<networking>disable</networking>
</configuration>Microsoft’s sandbox config guide lists all the parameters. So, rather than explain them individually, I’ll just provide some examples of customized sandboxes here.
Create a Max Security Sandbox
This configuration minimizes the attack surface of the sandbox. Copy it:
<Configuration>
<vGPU>disable</vGPU>
<Networking>disable</Networking>
<ClipboardRedirection>disable</ClipboardRedirection>
<AudioInput>disable</AudioInput>
<ProtectedClient>enable</ProtectedClient>
</Configuration>Enable any one way to share files to the sandbox (networking, clipboard, or mapped read-only sharing as shown below).
Save the config as a .wsb file.
Map Downloads to Sandbox
I have a folder named ‘sus’ where I keep downloads I don’t initially trust. I use this config to mount this folder inside the sandbox:
<Configuration>
<MappedFolders>
<MappedFolder>
<HostFolder>C:\Users\anup\Downloads\sus</HostFolder>
<ReadOnly>true</ReadOnly>
</MappedFolder>
</MappedFolders>
<LogonCommand>
<Command>explorer.exe C:\Users\WDAGUtilityAccount\Desktop\sus</Command>
</LogonCommand>
</Configuration>I’ve also used the LogonCommand parameter. So, this sandbox mounts the sus folder as read-only and automatically opens it at startup.
Run Scripts & Install Apps at Startup
If you’re a command-line aficionado, you’ve likely saved a few scripts to save time. These could be scripts to automate registry tweaks, to change the IP address or DNS, and so on.
Refer to the previous example. Mount the folder containing the script file and use LogonCommand to autorun the script at startup in the same way.
You can also launch executables and auto-install apps at startup with this method.
Add Sandbox to Right-Click Menu
Run in Sandbox is a popular sandbox upgrade by Damien Van Robaeys. It adds multiple options to the right-click context menu so that you can open files in a sandbox more easily.
- Download the archive from GitHub on the host PC.
- Extract the files.
- Press Win + X and select Terminal (Admin).
- Switch to the extracted directory with
cd. - Enter
.\Add_Structure.ps1 -NoSilentto run the script.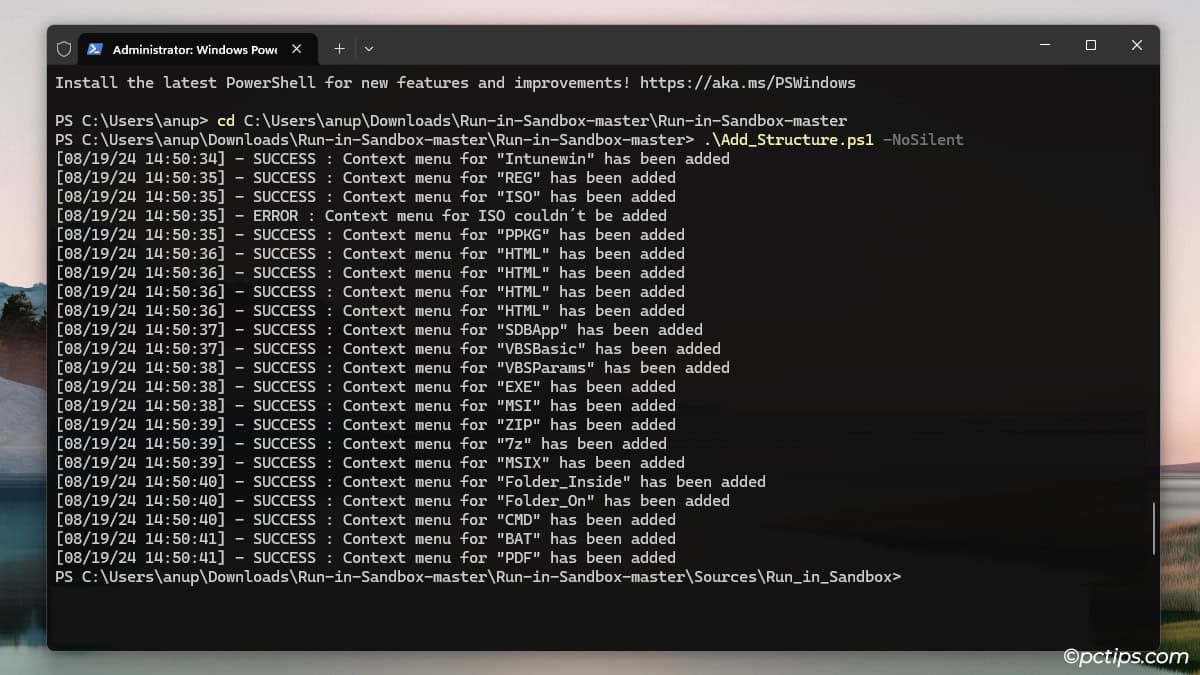
- The script should add context menu options for file types like EXE, MSI, PDF, ZIP, BAT, etc. Feel free to try them out.
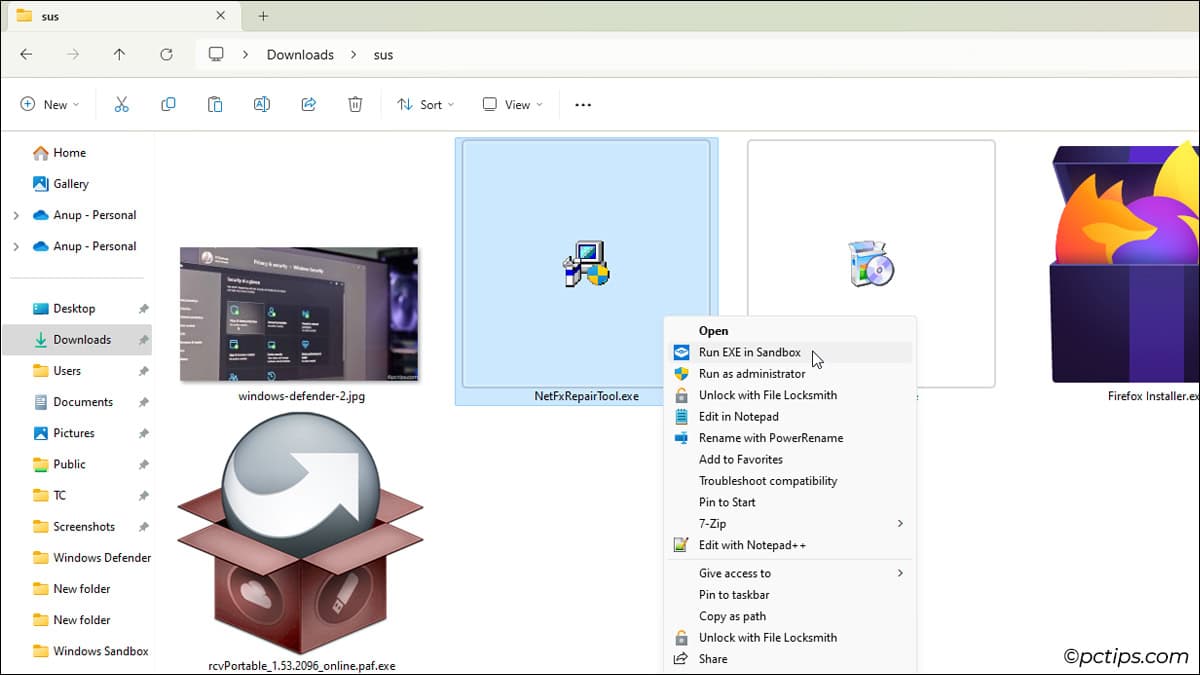
If you feel that it added options for too many file types, you can trim down the list.
- Go to
Run-in-Sandbox-master\Sources\Run_in_Sandboxin File Explorer. - Open
Sandbox_Config.xmlwith Notepad. - Set the nodes you want to remove to
Falseand save the changes.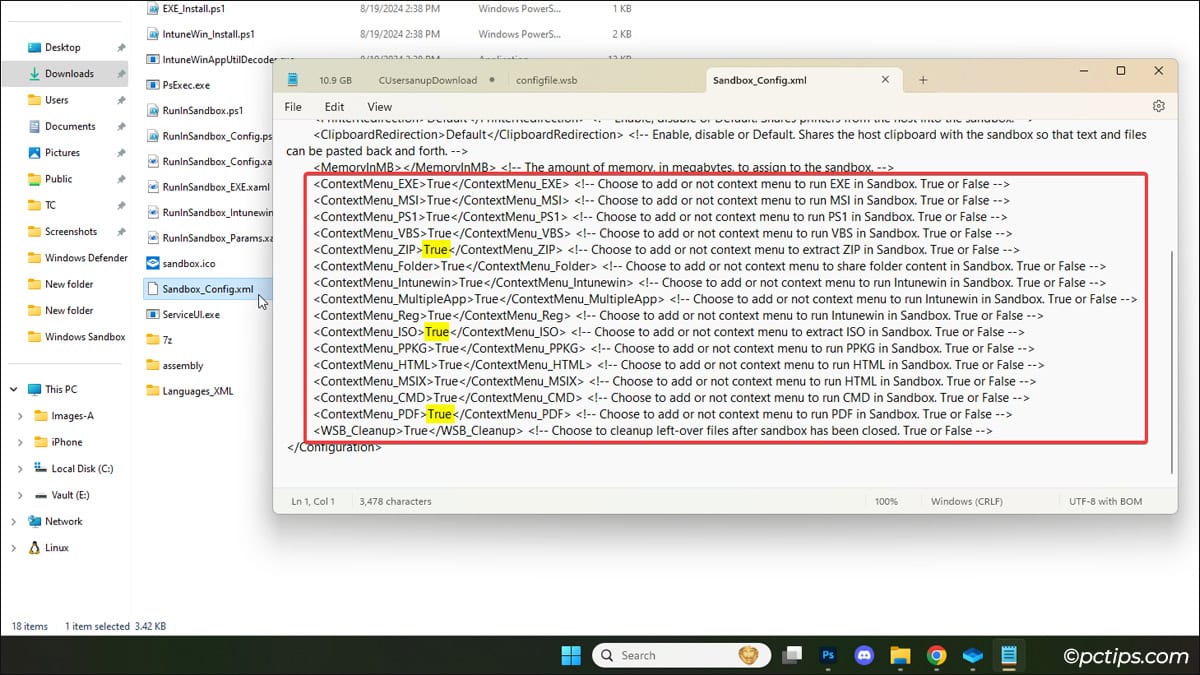
And if you ever want to undo all these changes, follow steps 3 and 4 from earlier. Then, run the remove script with .\Remove_Structure.ps1.
Run Sandbox Inside a VM
If your hypervisor supports nested virtualization, you can even use Windows Sandbox inside a Virtual Machine (VM).
A VM inside a VM, kind of like a Matryoshka doll.
I have a few VMs with lots of personalized settings. I don’t like making them the scapegoat for threat-testing. In cases like that, having access to Windows Sandbox inside the VM is useful.
But that’s still a rare use case. Enterprise environments that use VMs on a large scale are where this feature really shines.
Windows Sandbox vs Alternatives
There are three main alternatives to Windows Sandbox:
- MS Defender Application Guard
- Third-party sandbox apps
- Hypervisors and full-featured VMs
I recently covered app-guard in my Windows Security guide. This adds an isolation feature to MS Edge and Office. This feature is even faster than Windows Sandbox if you specifically need to test sketchy links and documents.
Among third-party alternatives, Sandboxie is a classic time-tested tool with lots of useful features.
VMs can also be excellent depending on your needs. You could use Windows Hyper-V or third-party hypervisors like VirtualBox or VMware.
VMs are extremely similar to a real Windows install. They persist after closing and provide almost all features including Windows Security. They’re much better for long-term testing and malware monitoring.
The downside is that they’re not as quick and convenient and require a lot more configuration and resources.
Overall, Windows Sandbox is an excellent feature for most users. It brings the best of all worlds.
Hopefully, this guide helped you understand why you should add it to your toolbox and how to use it fully.
Please give the guide a share if you found it useful. And if you have any questions, let me know in the comments!