20 Privacy Mistakes Everyone Makes (And How to Fix Them)
Last Updated:
We all value our privacy, but are you really doing everything you can to protect it online?
I’ve spent countless hours testing privacy tools, reading terms of service, and learning from my own mistakes.
I’ve found that most people are still making some critical mistakes.
Let’s dive in and see if you’re guilty of any of these privacy no-no’s!
Oversharing on Social Media
I get it, your avocado toast looks amazing.
But do you really need to tag the cafe, share what you’re doing later, and mention that you’ll be out of town next week?
You’re making it way too easy for creeps to stalk you in real life.
Here are a few things you should never post on social media:
- Your full birthdate
- Your home address
- Your phone number
- Vacation plans (wait until you’re back to post those beach pics!)
- Anything work-related that could be considered confidential
For more tips on what to keep off the ‘gram, check out my article on 20 Things to Never Share Online.
Posting Pictures with Metadata
That innocent selfie could be giving away more than your good side.
Many photos contain embedded metadata that can reveal:
- The exact location the photo was taken
- The date and time
- The device used
- Even the name of the photographer
Before posting any photos, strip out the metadata using a tool like ImageOptim (Mac) or EXIF Purge (Windows).
Pro tip: Disable geotagging on your phone’s camera so location data isn’t recorded in the first place.
Sending Sensitive Info via Text or Chat
We’ve all gotten a bit too comfortable texting and chatting.
But the reality is, standard SMS texts and many chat apps are not secure ways to send sensitive information like:
- Passwords
- Credit card numbers
- Bank account details
- Private photos
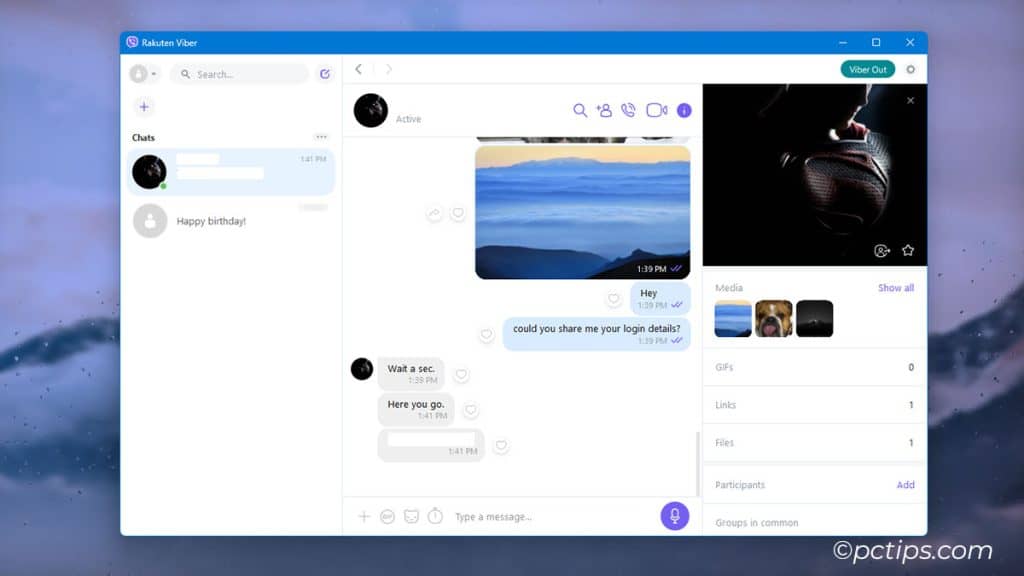
For truly sensitive convos, use an end-to-end encrypted messaging app like Signal.
Bonus tip: Enable disappearing messages so your private chats vanish after they’ve been read.
Not Using a Password Manager
If you’re still trying to remember all your passwords, you’re doing it wrong.
Not only is it a huge hassle, but it often leads to weak, easily-guessed passwords.
A password manager like bitwarden can create strong, unique passwords for every account and securely store them for you.
All you have to remember is one master password.
And please, NEVER use any of the passwords on this “100 Most Common” list.
Instead here’s a guide to create super strong passwords.
For maximum security, enable two-factor authentication on your password manager and any other critical accounts (email, banking, etc.).
This adds an extra layer of protection even if your password is compromised.
Ignoring Software Updates
You know that annoying “Update Available” notification? Don’t ignore it!
Software updates often include critical security patches that fix vulnerabilities hackers could exploit.
The longer you wait to install updates, the longer your device is at risk.
Action step: Turn on automatic updates for your operating system and key programs like your browser and anti-virus software.
Saving Passwords in Your Browser
Those browser prompts to save your password are mighty tempting.
But your browser’s built-in password manager is nowhere near as secure as a dedicated password manager.
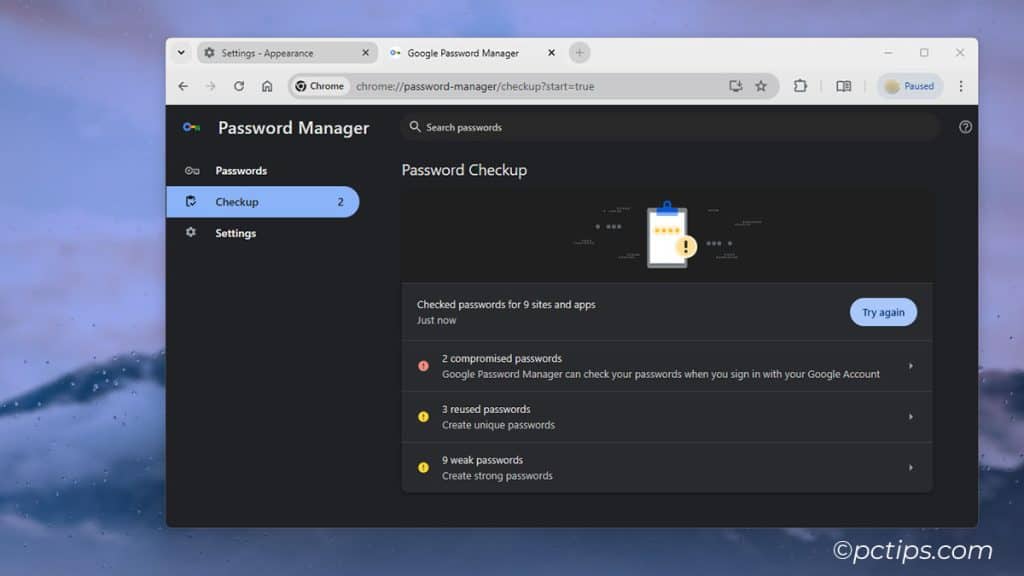
In Chrome, Edge, and Firefox, all your saved passwords are visible in plain text to anyone who has access to your computer. Yikes.
Do yourself a favor and switch to a real password manager.
I promise the slight inconvenience is worth the security boost.
Must Read Article: “Password Safety: Are You Making These 20 Critical Mistakes?”
Trusting Incognito Mode Too Much
Incognito mode: not as sneaky as you might think.
While it does delete some data, like cookies and your browsing history, it’s far from a silver bullet.
Your ISP, the sites you visit, and any snooping bosses or governments can still see your activity.
And if you accidentally log into an account, like Google or Facebook, they can tie your activity back to you.
Bottom line: incognito is handy for hiding embarrassing searches from your spouse.
But for real privacy, you need more robust tools like Tor or a VPN.
Not Using a Privacy-Focused Browser
If you’re still using Chrome or Safari, your privacy could be at risk.
These mainstream browsers are infamous for collecting user data to serve up targeted ads.
For a more private browsing experience, try a browser that puts privacy first.
Personally, I use LibreWolf, which is based on Firefox but with enhanced privacy features and tweaks.
Brave is another solid option, which blocks trackers and ads by default.
Want to go full tin-foil hat?
Check out the Tor browser.
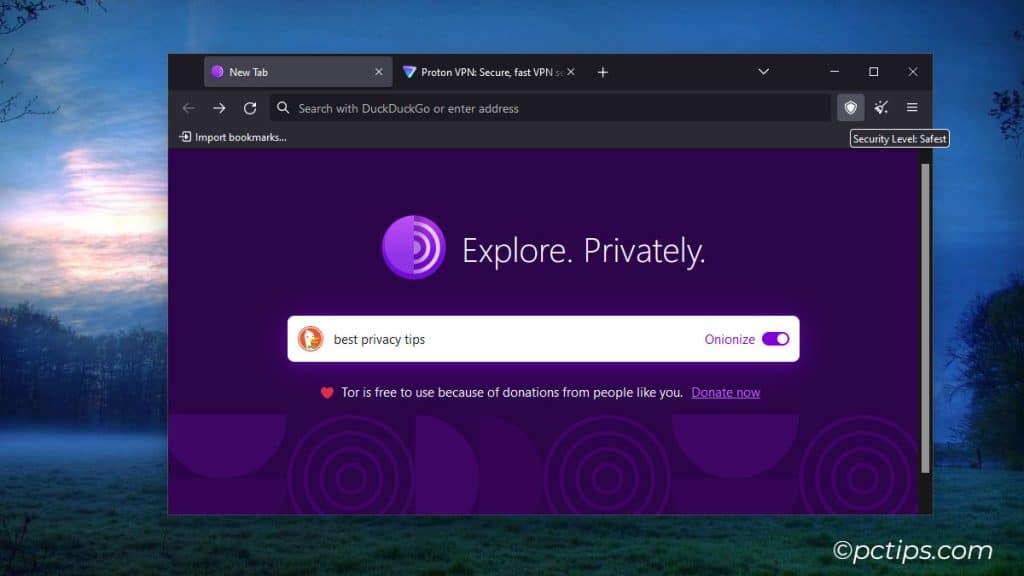
It routes your traffic through multiple nodes, making it very difficult to trace your activity.
It’s overkill for everyday browsing, but handy if you need maximum anonymity.
Searching with Google
Google has become synonymous with web searching, but it’s also synonymous with data collection.
Every search you make is logged, analyzed, and used to build a uncomfortably detailed profile on you to target ads.
Fortunately, there are several privacy-respecting search engine alternatives:
- DuckDuckGo: Doesn’t track you or collect any personal info.
- Startpage: Gives you Google search results without the tracking.
- Qwant: A European search engine that respects user privacy.
Switching is easy – just set your new search engine of choice as the default in your browser. You might be surprised at how little you miss Google.
Plugging in Random USB Drives
You know that pile of free flash drives you’ve collected from conferences and trade shows?
Yeah, don’t plug those into your computer. Like, ever.

Here are some examples of how a bad actor could use a rogue drive to wreak havoc:
- Installing a keylogger to capture your passwords and other sensitive info
- Encrypting your files and holding them for ransom
- Stealing files off your hard drive
- Taking over your webcam and mic to spy on you
Be cautious about what you stick in your ports!
If you have old USB drives lying around then check out these 20 Genius Ways to Use a USB Drive .
Using Public Wi-Fi
Free Wi-Fi is awesome – it saves data and keeps you connected on the go.
But public networks are also a hacker’s playground.
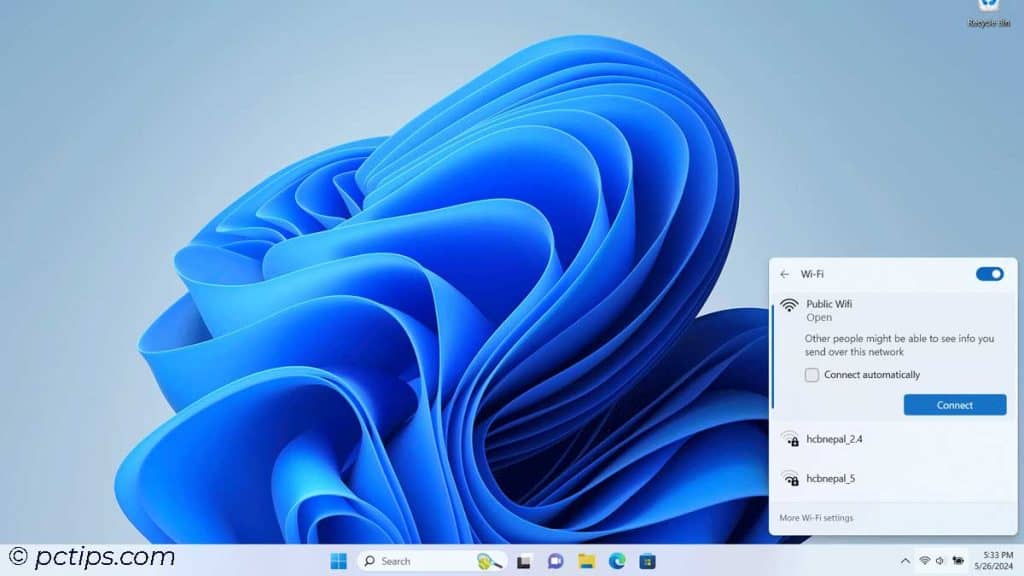
On an unsecured network, a bad actor could:
- Spy on your online activity
- Intercept your login credentials
- Redirect you to malicious websites
- Steal files you send or receive
- Infect your device with malware
The solution? Always use a virtual private network (VPN) when connecting to public Wi-Fi.
A VPN encrypts all your internet traffic, making it unreadable to anyone who might be snooping.
There are tons of great VPN options out there, but a few I’ve personally tested and recommend are:
Just make sure to pick a reputable provider – free VPNs are often worse than no VPN at all.
Don’t forget about your home network! Make sure your router is set up with strong encryption (WPA2 or WPA3) and a hard-to-guess password. For bonus points, hide your network name (SSID) so it’s not broadcasting to every passerby.
Leaving Your Webcam Uncovered
Ever get the uncanny feeling you’re being watched through your webcam?
It’s rare, but webcam snooping does happen.
There have been some high-profile cases of webcam snooping, like:
- Schools secretly monitoring students at home through school-issued laptops
- A hacker spying on Miss Teen USA through her webcam
- A major flaw in Zoom that let sites forcibly join you to a call with your camera on
Luckily, protecting yourself is as simple as covering your camera lens when not in use.

You can use a piece of tape or a cute little slider made for this purpose.
For more peace of mind, check out my guide on How to Secure Your Webcam.
Using Your Primary Email for Everything
Your email address is the key to your online identity.
If a hacker gets into your primary inbox, they could easily reset passwords and break into your other accounts.
That’s why it’s smart to use separate email addresses for different purposes, like:
- A primary address for important things (banking, health, work, etc.)
- A secondary address for semi-important things (shopping, social media, etc.)
- A throwaway address for one-time signups, email lists, etc.
This way, if one address is compromised, the damage is contained.
Pro tip: Add a “+” and a unique word to your email address when signing up for new accounts (e.g. [email protected]). You’ll still get the messages, but you can easily filter them and see which companies are spamming you or selling your info.
Like this tip? here are 35 more gmail features you might like.
Not Locking Your Devices
Stepping away from your computer or phone?
Lock it. Every. Single. Time.
It only takes a minute for a snooping coworker, curious toddler, or thief to wreak havoc on an unlocked device.
Get in the habit of hitting Windows+L on your PC and using a passcode or biometric lock on your phone and tablet.
Here are 100 most useful keyboard shortcuts you might want to try out.
On a Mac?
Try Control+Command+Q to quickly lock your screen
Falling for “Shoulder Surfing”
You’re working on a sensitive doc in a crowded coffee shop.
You’re so engrossed, you don’t notice the nosy Nancy peering over your shoulder.
Congrats, you’ve just been “shoulder surfed“!
Low-tech snooping is still a real threat, especially in public spaces.
To thwart looky-loos, invest in a privacy screen.
These thin films stick to your laptop or phone screen and make it unreadable from an angle.
I like these screens from 3M.
When in public, also be mindful of what you’re working on.
Save the sensitive stuff for home or the office.
And always lock your screen if you step away, even for a minute.
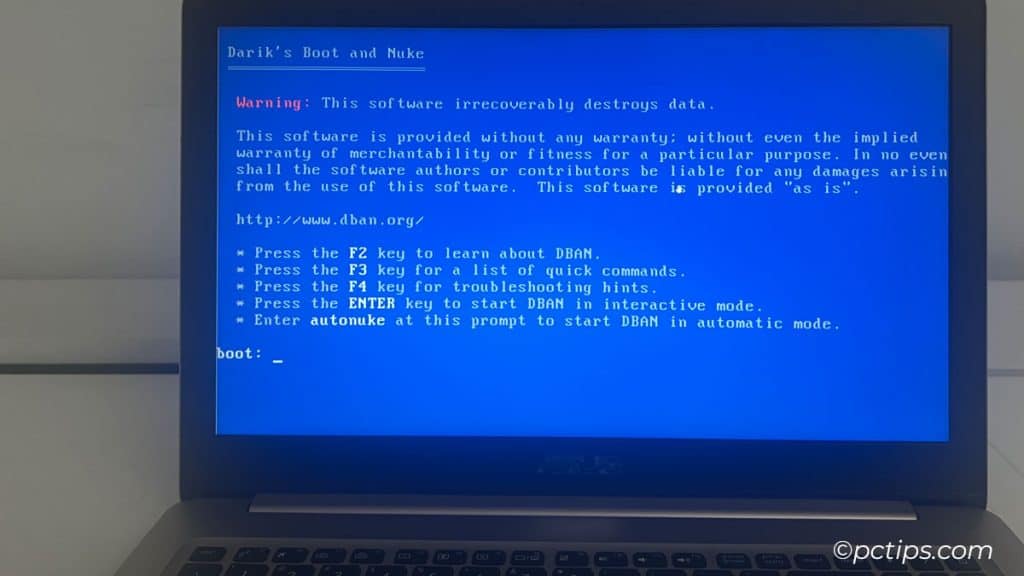
Recycling Electronics Without Wiping Them
Donating or recycling your old devices is great for the planet.
But if you don’t properly wipe them first, it could be disastrous for your privacy.
Even if you delete files or do a factory reset, your data could still be recoverable by someone who knows what they’re doing.
The only surefire way to protect your info is to do a secure erase before getting rid of any device. Here’s how:
- On a computer: Use disk wiping software like DBAN to overwrite your entire hard drive with random data. This makes recovery impossible.
- On a phone/tablet: Encrypt your device before doing a factory reset. This scrambles your data so it can’t be read even if recovered.
A little prep work can save you from a major privacy breach down the road.
Not Deleting Old Accounts
Remember that forum you joined years ago to ask one question and never went back?
Or that app you tried once and forgot about?
Chances are, those accounts are still floating around out there with your personal info.
Unused accounts are low-hanging fruit for hackers, who can use the data to craft targeted phishing attacks or even steal your identity.
Plus, if the service gets breached (which seems to happen a lot these days ), your info could end up in the wrong hands.
Do a periodic purge of any accounts you no longer use. If possible, delete them entirely.
If not, at least remove any sensitive info and change the password to something unique.
Not Reading Privacy Policies
I know, privacy policies are about as exciting as watching paint dry.
But blindly clicking “I agree” could be putting your data at risk.
Many apps and websites bury sketchy data practices in pages of dense legalese, hoping you won’t bother to read it.
Things like:
- Selling your personal info to third parties
- Tracking your location even when the app is closed
- Accessing your contacts, photos, and other sensitive data
It’s important to know what you’re signing up for. Before agreeing to any privacy policy, skim it for red flags like:
- Vague language about how your data will be used
- Mentions of sharing data with unnamed “partners” or “third parties”
- Anything that makes you feel icky or uncomfortable
If something seems shady, don’t be afraid to take your business elsewhere.
There are usually plenty of competing services with better privacy practices.
Falling for Phishing Scams
Phishing is one of the most common types of online scams.
It usually involves an email, text, or social media message that looks legit but is actually a trap to steal your info.
Common phishing tactics include:
- Fake urgency: Messages that try to scare you into acting fast, like “Your account has been locked!”
- Too-good-to-be-true offers: Things like free gift cards, inheritances from long-lost relatives, or get-rich-quick schemes
- Generic greetings: “Dear valued customer” instead of your actual name
- Mismatched URLs: Links that don’t match the company’s real domain
If you get a message that seems even a little off, don’t engage!
Hover over any links (without clicking!) to see where they really lead.
When in doubt, go directly to the company’s website to check if the message is legit.
For more tips, check out my guide on 21 Ways to Tell if a Link is Safe Before You Click.
Thinking “It Won’t Happen to Me”
Perhaps the biggest privacy mistake of all is assuming you’re not a target.
Many people think “I’m not important enough to hack” or “I have nothing to hide, so why bother?”
But the truth is, every single one of us is at risk.
Adopting a few simple privacy habits can save you a lot of headaches down the road.
How many are you guilty of? No judgment, we’re all learning.
The important thing is taking steps to do better.
Start with the tips that seem easiest and work your way up.
P.S. If you found this article helpful, please consider sharing it with your friends and followers. You never know who might need a little privacy wake-up call.
Can you help find the best data removal service? thnx!!