Is Your Password on the Dark Web? Check Now
Last Updated:
Your password is probably on the dark web. Yep, you heard me right.
But don’t panic just yet!
Hackers often sell huge lists of stolen login credentials on the dark web.
The good news? You can easily check if your passwords have been compromised.
And I’m going to show you exactly how to do it.
But first, let’s cover some basics…
What is the Dark Web?
The “dark web” sounds like something out of some science fiction, but it’s a real thing.
The dark web is a hidden part of the internet that is not indexed by conventional search engines and you can’t access it with a regular browser.
It’s only accessible by specialized web browsers like Tor.
While the dark web has plenty of legitimate uses, it’s also a haven for illegal activity.
This includes the buying and selling of stolen login credentials.
When a major company gets hacked, there’s a good chance the looted data will end up for sale on a dark web marketplace.
How Do Passwords End Up on the Dark Web?
Typically, your password ends up on the dark web after a data breach.
When a company’s database is hacked, cybercriminals can steal sensitive information like email addresses and passwords.
They then sell this data to the highest bidder on the dark web.
Even if you practice good password hygiene, your credentials could still be compromised if a site you use is hacked.
That’s why it’s a must to regularly check if your passwords have been leaked.
Here are some of the best options:
Putting “Have I Been Pwned” to the Test
I decided to run a little experiment on myself.
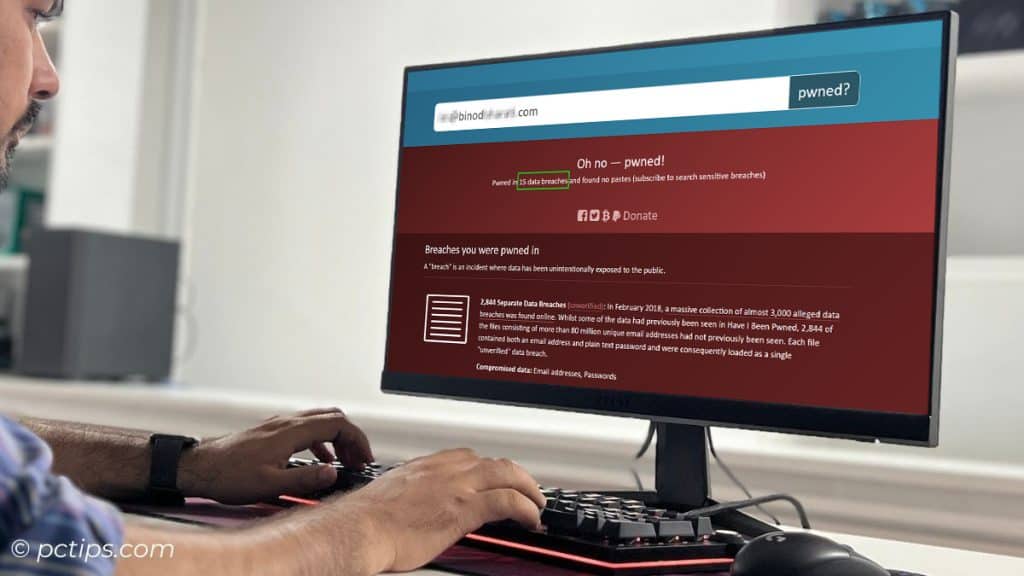
I plugged my email address into Have I Been Pwned and held my breath.
The result? My email was found in 15 different data breaches! 😳 Yikes.
But here’s the really cool part – Have I Been Pwned doesn’t just tell you that your info was breached, it tells you exactly which breaches it was found in.
Apparently, my data made appearances in the LinkedIn breach, the Twitter breach, my local ISP breach, and even the infamous Collection #1 breach that contained a whopping 773 million email addresses.
How to Use Have I Been Pwned
- Go to https://haveibeenpwned.com and enter your email address.
- Click the “pwned?” button. (Fun fact: it’s a play on “owned”)
- Check the results. If your email comes up, it will show you a list of known data breaches that include your info.
- Have I Been Pwned uses something called “k-anonymity” so it never actually stores your plaintext password – smart!
- Change your password immediately for any accounts on the list!
But wait, there’s more!
Have I Been Pwned also has a feature called Pwned Passwords.
Instead of searching by your email, you can type in any password and see if it appears in their database of hundreds of millions of real-world passwords exposed in data breaches.
Here’s how:
- Go to https://haveibeenpwned.com/Passwords
- Enter a password you want to check
- It will tell you how many times that password has shown up in their database of breaches (ideally it’s zero!)
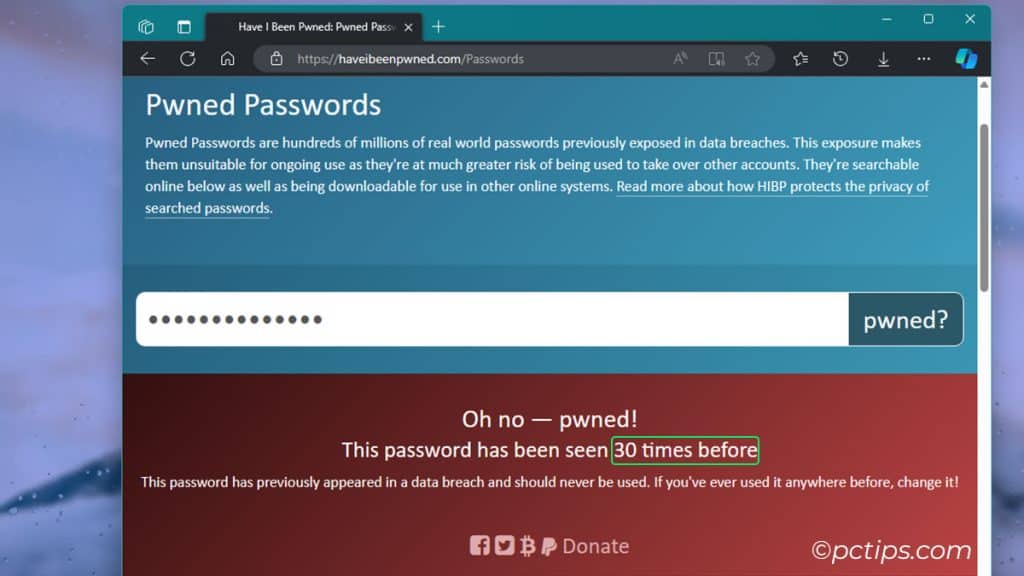
This tool is best for checking if your go-to passwords are compromised.
You can also use to check how secure a new password you’re considering might be.
If it shows up on the list, that means it’s been compromised before and you should pick something else.
Firefox Monitor
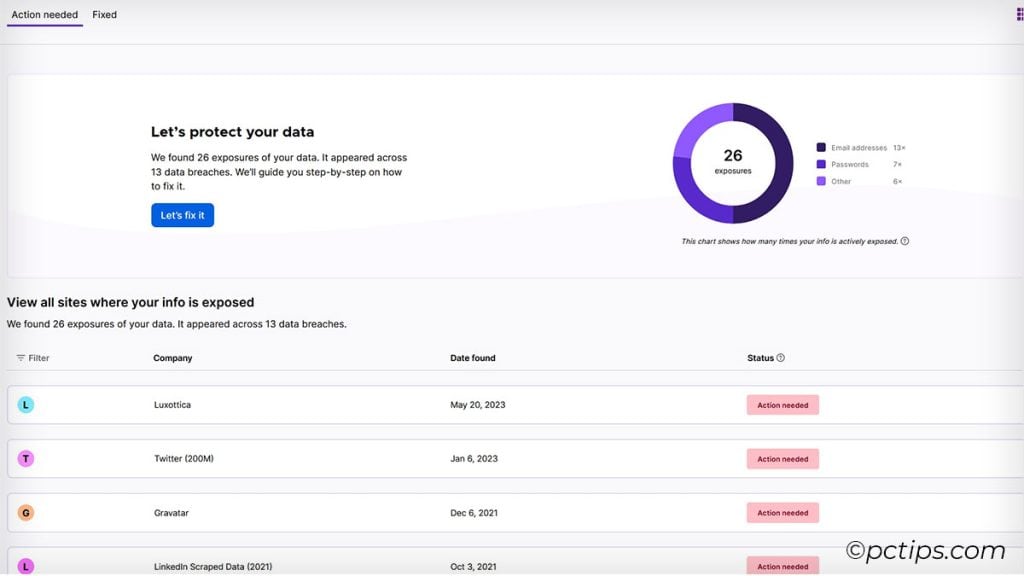
Firefox Monitor is a free service from Mozilla that tells you if your email has been swept up in a known data breach.
I like it because it gives you a little more detail than Have I Been Pwned.
Here’s how to use it:
- Go to https://monitor.mozilla.org in your Firefox browser
- Enter one or more email addresses (up to 5) and click “Check for Breaches”
- If results are found, it will tell you which emails were included in known breaches
- Click “More about this breach” for details on each incident
There’s also an option to sign up for alerts if your email is found in future breaches.
I highly recommend this!
Google Password Checkup
Did you know Google has its own password checkup tool?
Yep, if you use Chrome or have a Google account, you can easily see if any of your saved passwords have been compromised.
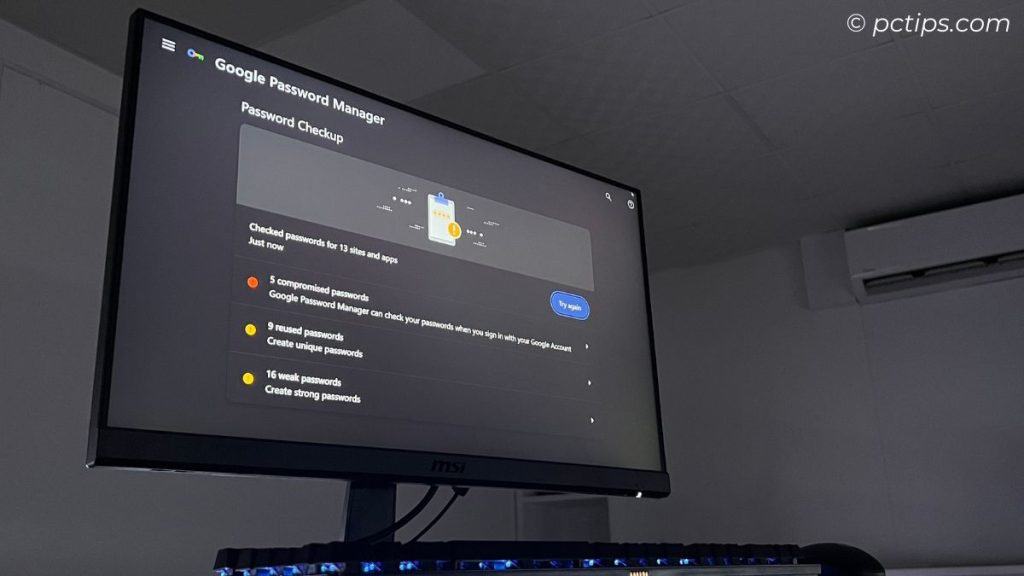
For Chrome users:
- Launch Chrome and go to
chrome://password-manager/passwords - Go to “Checkup” and click on Try again.
- If any come up as compromised, you’ll see a “Change password” button to quickly update them.
If you don’t use Chrome but have a Google account, you can run a similar scan at https://passwords.google.com.
This page will flag not only compromised credentials, but also passwords that are weak or reused across multiple sites.
Super useful for identifying which accounts need some password TLC!
Password Managers
Using a password manager is one of the best ways to up your online security.
Along with generating strong passwords and storing them securely, many password managers can also alert you to breached accounts.
For example, 1Password has a “Watchtower” feature that keeps an eye out for passwords that appear in known breaches.
Dashlane has a similar “Dark Web Monitoring” function.
If you’re not using a password manager yet, this is another great reason to start.
DeHashed
DeHashed is a searchable database of leaked credentials from the dark web.
While it’s primarily aimed at security researchers and professionals, anyone can use the free version to check if their information has been leaked.
To use DeHashed:
- Go to dehashed.com
- Enter your email address or username in the search bar
- If your information is found in their database, you’ll see details about the specific leaks it was involved in
Keep in mind that DeHashed is a paid service for full access, but the free search can still give you valuable insight into whether your credentials have been leaked.
You’ll still need to create an account to access the search feature.
Manual Breach Checks
If you want to get hands-on, you can also manually check through recent data breach records to see if any of your accounts were impacted.
Some of the most notable breaches in the past few years include:
- Facebook (2021) – 533 million users
- LinkedIn (2021) – 700 million users
- Collection #1 (2019) – 773 million unique emails and 21 million passwords
- Yahoo (2013-2014) – 3 billion user accounts
- Adult Friend Finder (2016) – 412 million accounts
- Heartbleed (2014) – Impacted up to 500k sites using OpenSSL
If you had an account with any of those services during the noted periods, there’s a decent chance your password was leaked.
Other major breaches: Equifax, MySpace, eBay, Adobe, Target, Uber, Home Depot, Anthem… the list goes on.
It’s a good idea to regularly google “Company Name + data breach” for any sites you have an account with, especially those housing your sensitive personal info.
I Found My Password on the Dark Web, Now What?
First of all, don’t freak out. You’re not the first person this has happened to, and you won’t be the last.
But you do need to take action ASAP:
- Change your password on the affected site(s). Like right now. Use a strong, unique password. None of this “123456” or “qwerty” nonsense.
- If you haven’t already, enable two-factor authentication (2FA) on important accounts like email, banking, social media, etc. That way even if a hacker has your password, they still can’t get in without access to your phone.
- Check to see if you used that same password on any other sites. Change it everywhere. A password manager really comes in handy here.
- Stay alert. Having your credentials leaked puts you at higher risk for phishing attempts and identity theft. Keep an eye on your email and bank statements for any suspicious activity.
- Get in the habit of regular password checkups. I’d recommend checking your details on HaveIBeenPwned and running a Password Checkup scan every few months. It only takes a minute and could save you a huge headache down the road.
Finding out your password is on the dark web can be scary, but don’t let it keep you up at night.
By taking the proactive steps mentioned above you can minimize your risk and sleep a little easier.
So, have you checked if your passwords are on the dark web? Did you find any surprises?
And if you found this article helpful, consider spreading the word.
Send it to your friends who still use “password123” for everything. Share it in your group chat.
The more people know how to check for compromised passwords, the better off we’ll all be.