Are Password Managers Really Safe? My Honest Opinion & In-Depth Analysis
Last Updated:
In my recent roundup of the best password managers, I did extensive testing of all the top options.
But one question kept coming up from readers: are password managers REALLY safe?
It’s a valid concern.
After all, you’re putting ALL your most sensitive logins in one place.
Is that really a good idea?
I hear you. And I want to address this head-on.
Let’s dig in.
How Password Managers Work
First, a quick refresher on what password managers actually do:
- You create one “master password“
- Your individual site logins are encrypted with this master password
- The encrypted data is stored either locally on your device or in the cloud
When you need to log into a site, the password manager decrypts the login using your master password and autofills it for you.
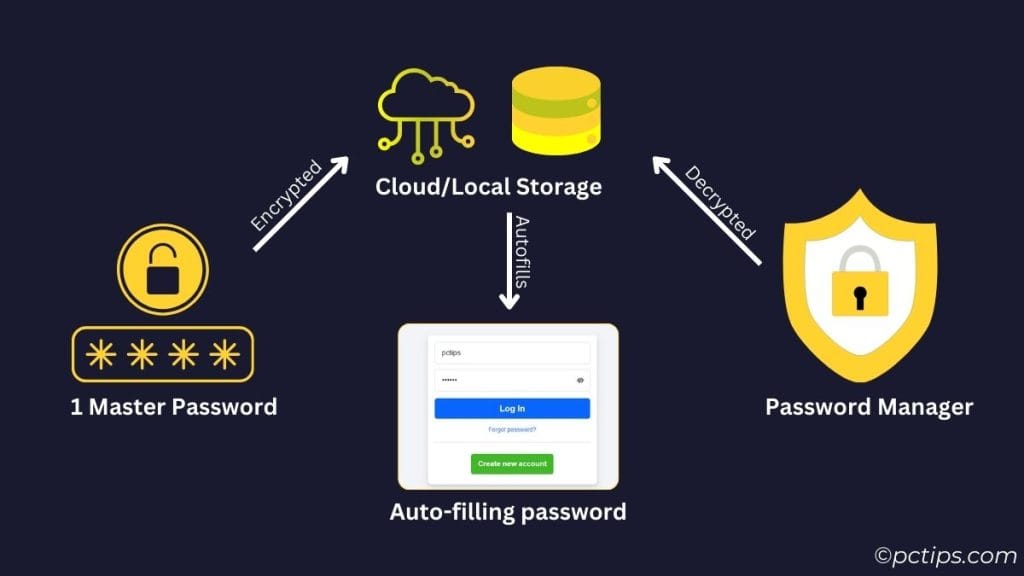
All the encryption and decryption happens locally on your device.
Even if you’re using a cloud-based password manager, the company itself can’t see your actual passwords – only the encrypted gibberish.
This is known as “zero-knowledge” architecture.
Potential Risks to Consider
There ARE some potential risks with password managers:
- If you forget your master password, you’re pretty much hosed (although some have contingencies)
- If your master password is guessed/hacked, the attacker has the key to ALL your other logins
- If the password manager itself has a security breach, your encrypted data could be exposed (Is Your Password on the Dark Web? Check Now)
- If there’s a flaw in the encryption method, a hacker could theoretically crack your vault
- If there are security vulnerabilities in the password manager’s software or browser extensions, attackers could exploit them
- If someone gets their hands on your unlocked phone or computer where you’re logged into your password manager, they have access to everything
There’s also the risk of a rogue employee at the password manager company accessing data they shouldn’t.
These are scary scenarios, no doubt about it.
But here’s the thing:
ALL of these risks also apply to NOT using a password manager!
Think about it:
- If you use the same password everywhere (like 84% of people do), one breach can domino across all your accounts.
- If you store your passwords in a plaintext file or on a sticky note and someone finds it, game over.
- If you rely on your browser’s built-in password manager, you’re at the mercy of their security practices (which are usually not great)
- If you rely on your memory, you’re likely to forget or mistype passwords frequently (54% of people STILL rely on memory)
You see where I’m going with this.
Using a password manager doesn’t make the risk worse – it substantially minimizes it compared to the alternatives.
Have Password Managers Ever Been Hacked?
The short answer is: Yes, but it’s not as bad as you think.
The most famous example is LastPass.
As I wrote in my previous article, they’ve had multiple breaches, including a nasty one in 2022 where hackers got ahold of customer vault data.

Sounds awful, right?
But here’s the crucial detail:
The hackers only got the encrypted data. Not the master passwords needed to unlock it.
To date, there’s no evidence that any LastPass customers’ passwords were actually cracked and exposed from this breach.
That’s the power of zero-knowledge encryption.
Even if attackers steal the password manager’s encrypted vaults, it’s all useless gibberish without the master passwords – which the company never has access to.
Other password managers like ProtonPass, Dashlane and RoboForm have had minor security flaws discovered (like browser extension bugs), but no major breaches.
And open-source managers like Bitwarden have the advantage of “many eyes” watching the code for potential vulnerabilities.
Of course, no software is unhackable.
Password managers are juicy targets, and attackers will keep trying to find flaws.
But the leading managers have a strong track record of quickly patching vulnerabilities and resisting breach attempts.
Why I (Still) Recommend Using a Password Manager
So with all these risks and scary breach stories, why do I still recommend using a password manager?
Because the benefits massively outweigh the risks:
- Unique passwords are a necessity in today’s breach-filled world. Password managers make it incredibly easy to use a different, strong password for every login.
- Encrypted storage is WAY safer than plaintext files, browser caches, sticky notes, or using one password everywhere.
- Autofill and auto-capture mean you don’t have the hassle of remembering and typing passwords (the average person has 168 passwords). It’s more convenient AND more secure.
- Built-in generators help you create long, random, unguessable passwords – far stronger than what most humans come up with.
- Secure sharing lets you safely share logins with family or coworkers without resorting to insecure methods like email or text.
- Automatic updates ensure your passwords are always in sync across all your devices.
- Security alerts (offered by some managers) will notify you immediately if any of your logins are found in a breach, so you can take action.
In short, password managers take the human error and hassle out of password security.
Using a reputable password manager is a massive security upgrade for the vast majority of folks.
What Makes a Password Manager Secure?
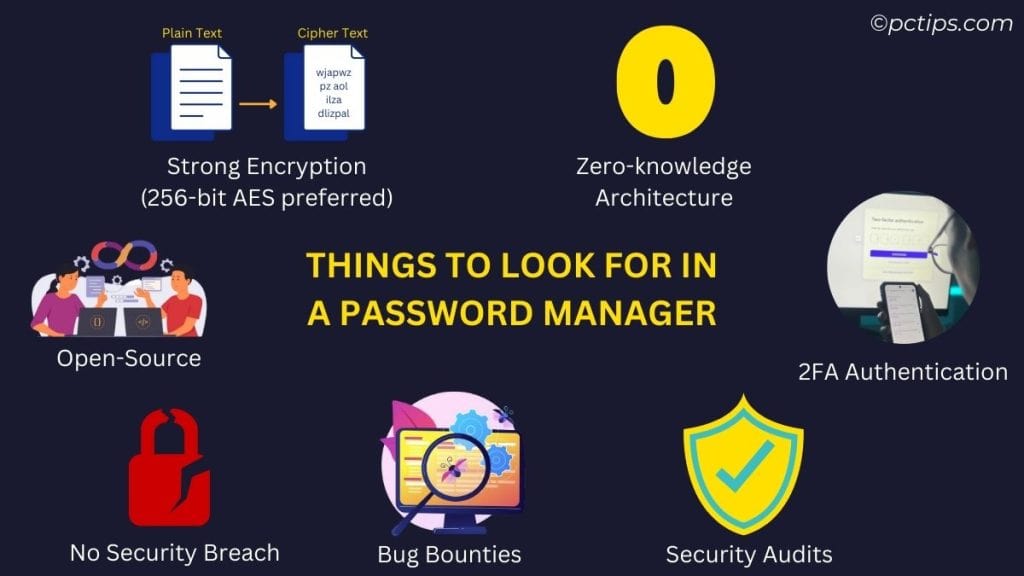
Alright, so we’ve established that password managers, while not perfect, are still a net positive for security.
But what separates the secure ones from the sketchy ones?
Here are the key factors I look for:
- Strong Encryption: 256-bit AES or equivalent to make brute-force cracking virtually impossible
- Zero-Knowledge Architecture: The company never has access to your unencrypted data
- Two-Factor Authentication: 2FA adds an extra layer of protection to your master password
- Regular Security Audits: Third-party experts should test the system for vulnerabilities
- Bug Bounties: Paying ethical hackers to find and report flaws is a sign of confidence
- A Clean Breach History: Has the company had major incidents? How did they handle them?
- Open-Source Code: Not required but allows for crowdsourced vulnerability checking
The top password managers I recommend – 1Password, NordPass, Bitwarden, etc. – check all or most of these boxes.
But you can also do your own research to find a manager that meets your specific security criteria.
The Weakest Link Is… You
According to Verizon’s 2023 Data Breach Investigations Report, 74% of all breaches involve some human element.
The biggest security risk to your password manager isn’t the software, the encryption algorithm, or the cloud.
It’s you.
Yep, human error jeopardizes more password databases than any fancy-pants hacking.
Things like:
- Weak master passwords that can be easily guessed or brute-forced
- Falling for phishing scams that trick you into entering your master password on a fake site
- Malware on your computer or phone that logs your keystrokes or spies on your screen
- Leaving your devices unlocked and unattended in public places
- Social engineering tactics where an attacker cons you into revealing your master password over the phone or email
So even if you use a top-tier password manager, sloppy personal security can still bite you.
The good news is, most of these risks can be mitigated with good security habits.
Handling a (Potential) Breach
So let’s say the worst happens. Your password manager gets breached like LastPass did.
What do you do? First, don’t panic.
If you’re using a reputable password manager with strong encryption, your actual passwords probably haven’t been exposed.
The attacker likely only has the encrypted vault data, which is useless without your master password.
Still, here are some steps I recommend if your password manager has been breached (or if you even suspect it might have been):
- Change your master password IMMEDIATELY. Do this even if the company says the master passwords weren’t exposed. Better safe than sorry.
- Enable two-factor authentication if you haven’t already. This way even if the attacker has your master password, they still can’t get in.
- Review your password manager’s security bulletins to understand exactly what happened and what steps they’re taking to fix it.
- Keep a close eye on your email and other important accounts for any signs of unusual activity. Enable 2FA on these accounts too, if possible.
- Consider changing high-value logins (like email, banking, etc.) as an extra precaution. The password manager should alert you if any sites are found to be compromised.
- Stay alert for any phishing emails or messages related to the breach. Attackers may try to trick you into revealing more info. (21 Tips to Check If a Link Is Safe Before You Click)
- Evaluate whether you still trust the company after seeing how they respond to the incident. If they’re not transparent or their practices seem sloppy, it may be time to jump ship.
The key is to stay calm and proactive.
Don’t let one breach scare you into ditching password managers entirely.
My Recommendations for Using a Password Manager (Safely)
Here are my top recommendations for using a password manager safely and effectively:
- Choose a reputable password manager with a track record of strong security
- Use a unique, generated master password and never reuse it anywhere else.
- Enable two-factor authentication on your password manager and any critical logins.
- Keep your master password safe – never share it or write it down insecurely.
- Stay alert for phishing attempts and never enter your master password on an untrusted site.
- Use the password manager’s random generator to create long, unique passwords for every login.
- Be prepared to change your master password if there’s ever a breach at your password manager company.
- Keep your devices themselves secure with good security practices.
If you follow these guidelines, you’ll be well-protected even if your password manager experiences a breach.
Is It Worth Paying?
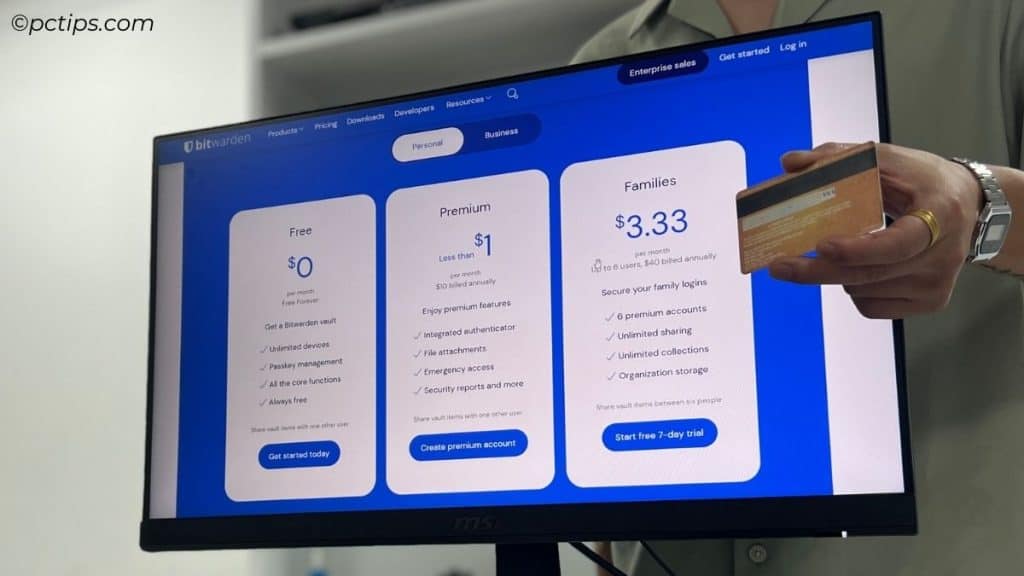
A lot of folks ask me: “Can’t I just use a free password manager? Why pay?“
It’s a fair question.
After all, some popular free options like Bitwarden and NordPass have a pretty robust feature set.
Nothing wrong with using a free tier, especially if you’re new to password managers and just want to dip your toe in.
But here’s why I think it’s worth ponying up for a paid plan:
- Extra security features: Paid plans often include stuff like Dark Web monitoring, encrypted file storage, more 2FA options, etc.
- Priority support: If you ever have an issue (especially a security issue), you want to be able to get help ASAP. Paid users typically get pushed to the front of the queue.
- More sharing options: Need to share logins with family or team members? Paid plans usually allow this; free plans are often limited to just one user.
- Supporting development: Password manager companies have a lot on their shoulders, security-wise. Paying them helps ensure they have the resources to keep making the product better and more secure.
- Long-term viability: If a “free” password manager shuts down… what happens to your passwords? A paid subscription ensures the company has a sustainable business model.
That said, a free password manager is absolutely better than no password manager.
But given how critical password managers are to online security (and how much work they save), I personally believe it’s money well spent.
Open-Source vs Proprietary Password Managers
Another common question I get:
Are open-source password managers more secure than proprietary ones?
Again, there’s no simple answer.
Both open-source and closed-source password managers have their pros and cons.
Open-source password managers like Bitwarden and KeePass have the advantage of transparency.
Anyone can audit the code for security flaws or backdoors. And there’s less risk of the company pulling a fast one on you.
On the flip side, open-source projects often have fewer resources for things like security audits, customer support, and slick user interfaces.
And just because the code can be audited doesn’t mean it always is.
Proprietary password managers like 1Password and Nordpass have the advantage of more resources and polish.
They can afford to hire top security talent, conduct frequent audits, and offer responsive customer support.
The downside is, you have to trust that the company is doing what it says it’s doing.
There’s no way for you to independently verify their security claims.
Personally, I think both open-source and proprietary password managers can be secure if they follow best practices like strong encryption, zero-knowledge architecture, and regular audits.
But if transparency is a top priority for you, stick with open-source.
If you prefer a more user-friendly experience, go with a reputable proprietary option.
My Top Picks (Again)
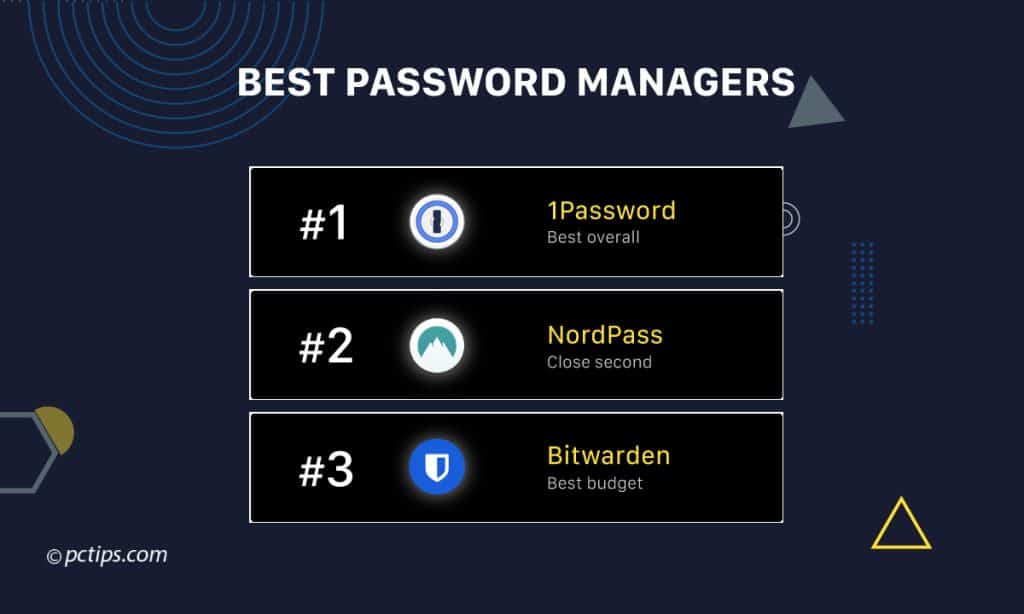
I covered this in much more detail in my password manager roundup, but if you just want a quick recommendation, here are my top picks:
- 1Password – Excellent security, elegant interface, tons of features. Great for families and teams.
- NordPass – Top-notch security, clean design, affordable prices. Some unique features like OCR scanning.
- Bitwarden – The best free option. Open-source with a premium feel. A bit more bare-bones than the others.
But honestly, any reputable password manager is better than no password manager.
The important thing is to pick one and actually use it!
So, Are Password Managers REALLY Secure?
Let’s bring this plane in for a landing, shall we?
YES, password managers are really secure – or at least, the good ones are.
They’re not perfect, and they’re not unhackable. Nothing is.
But the leading password managers are WAY more secure than the alternative (i.e. using weak, reused, or plaintext passwords).
They make it easy to follow best practices like using strong, unique passwords for every login.
And even if the password manager itself gets breached, your actual passwords are still safe thanks to strong encryption (assuming you chose a good master password).
Of course, you can’t just install a password manager and call it a day.
YOU still have to practice good security habits like:
- Choosing a strong, unique master password
- Enabling two-factor authentication
- Keeping your devices secure
- Staying alert for phishing attempts
- Being prepared to change your master password if there’s a breach
I hope you found this article helpful in evaluating password manager security!
If so, please bookmark it for later and share it with your friends.
Hi: I have totally enjoyed your posts and have learned sooooo much. Thank you. I have a question: Google is not saving my passwords any longer. When I clean my history they are all gone. No I do not have passwords checked. I have checked everything and it just does not save. How can I fix this. There is nothing compromising my computer.